What Chance Does your Company Have of Deflecting Hackers
The short answer is that nobody has any chance of preventing a network or web server from being hacked by guys who are sufficiently motivated by money, revenge, or getting fired from their job.
On the good side, very few of the companies and governments that have been hacked were hacked because there was an obvious hole in their network, the networking equipment, or even in the software on the network. Not even a rogue IT employee.
Almost every break-in occurred because an employee did something (accidentally) that gave the hackers the keys to the network.
So if we know that there's no way to stop a sufficiently motivated hacker from getting into our network, maybe there are some things that just shouldn't be on the network?
In the not too distant past there was very little information stolen from companies or the government. Why? There were no connections from the network to the Internet, and there were a very limited number of modems setup for remote access into the network.
Information between employees or customers was exchanged by phone, including voicemail, or by fax. While faxes and voicemail has certainly been hacked, the amount of damage that can be done that way is self-limiting. The amount of damage that can be done using stolen credentials of one employee is literally every piece of information the company owns. And probably lots of information from years gone by just because it's all stored on the network.
In the last few months Coke announced that they're doing away with voicemail at their headquarters, and JP Morgan (Chase Bank) decided to eliminate voicemail for 65% of its employees who are not customer facing.
That's kind of interesting, since after Sony was thoroughly hacked the only way they had to communicate between employees that was secure was by phone, voicemail or fax. Maybe not a great idea to eliminate fax and voicemail these days?
At this point there are two things you can do today to save your company a whole lot of grief:
1. Take anything off your network that isn't absolutely needed. Including old payroll records, old human resources records, old credit card transactions, old sales information, and old design information. Print them out and put them in file cabinets. Even though you'd be letting the information out of your company, it's way safer to send bankers boxes full of these records to a secure records storage company, than for it to be anywhere on your network. At this point it's not if the information will be stolen, it's when they'll be stolen.
You could also copy the files to huge hard drives (that are really cheap these days) and put them in a really secure fire safe in your office - or in a bank safety deposit box. You need at least three copies of each hard drive, and at least one of them should be somewhere other than where the other two are.
Storing your files on one of the "cloud" backup services is not secure. The cloud is not secure under any circumstances. If the hackers can break into Sony, the US Government, the Chinese Government, the Russian Government, they can break into any "cloud" service they want. There is a little safety if the files are encrypted where they are stored in the cloud, but you have no way of knowing that's how the files are actually stored at any particular cloud service. And any cloud service can go belly up and take/sell your files at any time. You have absolutely no recourse.
The cloud can make lots of things quick and easy. Storing super-secret information there isn't one of those things. It's just common sense.
Just because you can do something doesn't mean you should do it.
2. Limit the amount of email attachments your company receives and teach your employees what can be really dangerous when using the Internet.
Companies are sending office documents to other companies all the time. That's CRAZY! Every Word and Excel file can contain malware. Sending and receiving them on your own network amongst your own employees is reasonable. Opening the wrong Office file can cause malware to be immediately deployed.
So you think that your anti-virus software will catch something like that, right? Maybe. But there's a good chance that the malware in the Office file is too new for your anti-virus software to catch. In some cases, the malware can be crafted especially to be opened by someone in your company. Many of the companies hacked were targeted, and the malware sent via email to company employees was made just to infect that particular network to get the login information needed to allow the hackers free reign.
But wait... there's more!
Just visiting the wrong web page can run the same malware that you'd get by opening an Office file, Zip file, PDF, etc. All of these files can and have delivered malware to unsuspecting companies.
A few years ago programmers started using "pop-overs" (popovers) which overlay a part of or the whole screen with some type of call to action (also called a Lightbox)... Sign up for an email list, get a discount, take a survey or whatever. Popovers came into being because browsers were so good at getting rid of the older pop-up and pop-under ads that opened in a new window. The popover is a part of the webpage you're looking at - so there's essentially no way to stop it (so far?).
We're all used to seeing this request to take a survey from all kinds of sites:
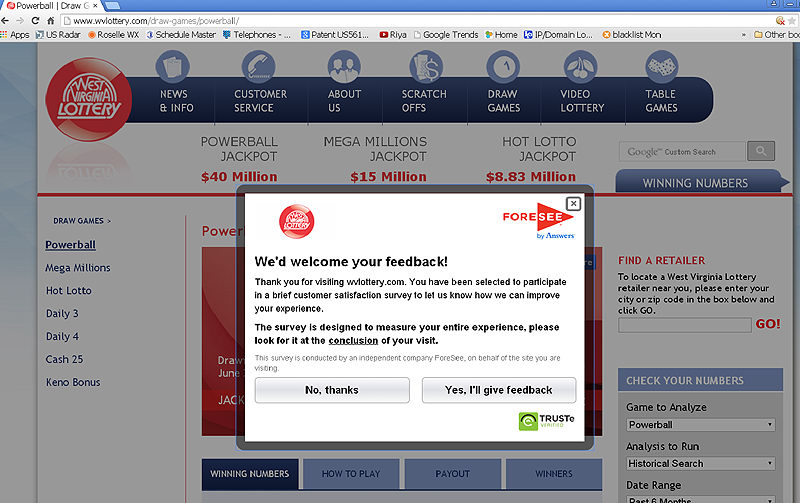
Everything you see overlaying the screen is dreamed up by a developer. The little X in the upper right corner doesn't tell your operating system to close the window. It just tells the "program" that popped it up there that you "want to" close it. As a developer, once you click that X or anywhere else on the overlay, including the parts around the box that darken the screen so you can't read what you were looking for under it, I can install malware on your computer and there's nothing you can do about it. My malware is specifically targeted at your company and hasn't been seen by your anti-virus software provider.
I'm just using this stupid survey popover as an example because we've all seen it maybe hundreds of times at well-known websites, and we've probably clicked to make it go away as many times. It's just a part of life on the web these days... But that's the problem.
If I wanted to get the keys to your network, I'd make a website that would be a copy of a real site that someone at your company would likely go to if I sent the link in an email, or I'd just make up a site that sounded like something someone in your company would go to. After a short time, I'd popup an exact copy of the survey request with the wording and logo changed for my fake site, including the meaningless logo for truste in the lower right corner. Even if I was Chinese or Russian and mis-spelled something in the box, or even had the totally wrong website name and logo in the box, it's unlikely you'd ever notice. You'd happily click somewhere, and I'd own your network.
But in this case there's no survey. Click OK, Not OK, Close, click anywhere you want, and I'd install malware on the computer which would start the process of letting me into every nook and cranny of your network with your secret company, financial and customer information. It's all mine after that one click where you told your computer that it's OK to download my program... except it's likely that many people in your company clicked that same link to the malware. There is nothing in the world you could do to stop me, although a modern operating system would probably ask you if you really want to install the program (the file name can look very innocuous so the user may very well click YES).
Because you can't stop all employees from clicking on a link with malware, go back and re-read #1 above... Don't keep anything on your network that you don't absolutely need.
But if you educate your employees that clicking on any link, no matter how official it looks or how many times they've seen it may be a really bad idea - it can't hurt.
I recently saw an email in my email quarantine that said our SAMS registration (allowing us to sell to the government) was about to expire. It actually does have to be renewed or something every once in a while, so I was surprised to see it in the quarantine. But when I put the mouse over the link it showed in the lower left side of my browser that I would really go to some goofy site name - not the real government SAMS site. You will generally be able to hover over a link and see where it's really going in a browser or email program, but you will never be able to see where you will be taken to clicking on any part of a popover.
If you see one of those stupid survey popovers, or almost any legitimate popover, you can pretty much tell if it's real by clicking the refresh button on the browser. The website you're visiting, and the survey company has put a cookie on your computer to let it know that you've already seen the popover. Most websites realize that showing you that popover more than once isn't going to make you want to come back there, so when you refresh the browser tab you are seeing the same page again, the page looks for the cookie which says you've already seen the ad today (or this hour), and it doesn't show you the popover again (for a while).
Never ever click on any part of the popover since you have absolutely no idea if the popover is real and taking you to a survey or where you can sign you up for a mailing list so you'll get a discount, or it's going to immediately install malware on your computer. I know what I'm looking at and I can't tell if a popover is legitimate or not without carefully looking at the source code for the webpage every time it pops over. I just hit the refresh button if I really want to see what's on the page, or I click Back and figure it's not worth the pain of being wrong and having malware installed on our network - which will take a painfully long time to detect and get rid of (if it can be gotten rid of). That one click can lead to long and painful days and nights where we may not even be able to do business, so there would be no money coming in and our customers wouldn't be able to get the equipment they need to finish their jobs.
Some really slimy developers write the code so you can't close a popover, or even leave a webpage. Never click on anything that page asks you to do, even if it says, "Do you really want to leave and miss this great opportunity." Close the whole browser and start over again. You'll be able to find most of the real tabs you were looking at in History. If you can't close the browser just reboot the computer. Don't click anything / anywhere when a website won't let you leave!

 Products
Products